Smartphone Users’ Family, Friends, and Other Enemies
The number of smartphone users worldwide was expected to surpass 2 billion in 2016. To protect personal and other sensitive information from unauthorized access, some smartphone users lock their phones. Yet, others don’t, risking the data and online services accessible through their devices. The risks emanate from both device thieves and those whobelong to the users’ […]
Predicting Smartphone Users’ Permission Decisions
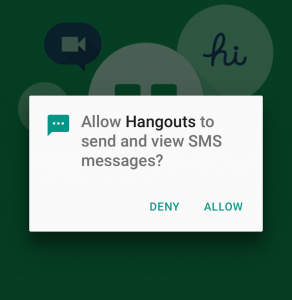
Current smartphone operating systems regulate application permissions by prompting users on an ask-on-first-use basis. Prior research has shown that this method is ineffective because it fails to account for context: the circumstances under which an application first requests access to data may be vastly different than the circumstances under which it subsequently requests access.
“I Don’t Use Apple Pay Because It’s Less Secure …”
This paper reports on why people use, not use, or have stopped using mobile tap-and-pay in stores. The results of our online survey with 349 Apple Pay and 511 Android Pay participants suggest that the top reason for using mobile tap-and-pay is usability. Surprisingly, for nonusers of Apple Pay, security was their biggest concern.
Social Insider Attacks on Facebook
Facebook accounts are secured against unauthorized access through passwords and device-level security. Those , however, may not be sufficient to prevent social insider attacks, where attackers know their victims, and gain access to a victim’s account by interacting directly with their device.
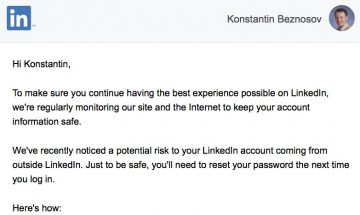
“I’m too Busy to Reset my LinkedIn Password”
A common security practice used to deal with a password breach is locking user accounts and sending out an email to tell users that they need to reset their password to unlock their account. This paper evaluates the effectiveness of this security practice based on the password reset email that LinkedIn sent out around May […]