Introduction
Various studies have shown that 40% or more of smart phone users do not use any authentication mechanism on their devices and most of the users cite “inconvenience” as the reason. [1,2].
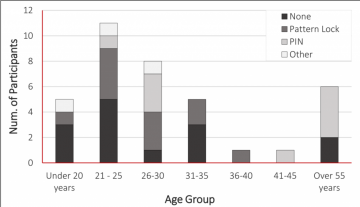
The “Age Group” – “Current Authentication Scheme” distribution. [3]
This entails that the usability issues of current authentication methods, has left a large proportion of smartphone users unprotected and in risk of data theft.
Continuous Authentication
Continuous Authentication (CA) has been proposed as a method of addressing the usability issues of current smartphone authentication methods. CA uses behavioural biometrics to continuously and transparently authenticate the user. Some examples of behavioural biometrics:
- The way users touch or swipe the screen
- The way users walk (gait patterns)
- Facial attributes
- Voice charachteristics
But while the idea of CA has been around for more than 10 years, none of the proposed CA schemes has seen a widespread implementation on one of the main mobile platforms.
This research aims at a comprehensive evaluation of proposed CA schemes to find the main issues hindering their widespread implementation :
- First a comprehensive set of evaluation criteria is presented.
- Then the proposed CA schemes are evaluated based on those criteria to find the main adoption issues.
References
[1] S. Egelman, S. Jain, R. S. Portnoff, K. Liao, S. Consolvo, and D. Wagner. Are you ready to lock? In ACM SIGSAC Conference on Computer & Communications Security. ACM, 2014.
[2] M. Harbach, E. von Zezschwitz, A. Fichtner, A. De Luca, and M. Smith. It’s a hard lock life: A field study of smartphone (un) locking behavior and risk perception. In Symposium on Usable Privacy and Security, 2014.
[3] H. Khan, U. Hengartner, and D. Vogel. Usability and security perceptions of implicit authentication: convenient, secure, sometimes annoying. In the proceedings of the 11th Symposium on Usable Privacy and Security (SOUPS), 2015.